U.S. companies lose between $225 billion and $600 billion annually due to intellectual property theft. Yet, most business leaders can’t clearly explain the difference between proprietary information and intellectual property—a confusion that leaves their most valuable assets vulnerable. IP-intensive industries accounted for 41% of the U.S. GDP in 2019, and in the tech sector, intangible assets comprise as much as 80-90% of enterprise value.
Businesses and any entity operating as a legal organization must implement robust contract management to safeguard proprietary information and intellectual property, ensuring that their assets and sensitive data are protected through structured, legally binding agreements.
The stakes are particularly high right now. Recent enforcement data show that IP theft cases increased by 21%, criminal arrests rose by 39%, indictments increased by 99%, and convictions rose by 29% compared to the prior year.
Meanwhile, in the wake of the DTSA, trade secret case filings jumped by roughly 30% from 2015 to 2017, and recent years have produced multiple nine-figure verdicts — at least five awards over $100 million from 2019–2023, including Appian’s $2.0 billion 2022 jury verdict (since vacated on appeal).
Understanding which protection mechanism applies to your assets isn’t academic—it determines whether you have enforceable rights or just wishful thinking when someone walks out your door with your company’s competitive advantage.
Proprietary vs Patented: Key Differences Between Proprietary Information vs Intellectual Property
The fundamental distinction comes down to legal foundation: Intellectual property receives formal legal protection (often automatically or via registration) under federal IP laws, creating exclusive rights that can be enforced in court. Proprietary information relies on contractual and secrecy-based protection—its value stems from being kept confidential, rather than from a government-granted right.
Intellectual property—which includes patents, trademarks, copyrights, and certain trade secrets—is backed by statutes such as the Patent Act and Copyright Act. These laws establish property-like rights that allow owners to stop others from using their creations without permission. These assets are often considered the exclusive property of their owner, and intellectual property rights are established to ensure enforceable property rights. For example, a U.S. utility patent grants a 20-year exclusive right in exchange for public disclosure of the invention, while a trademark can last indefinitely with proper use and renewal.
Patent infringement cases may result in monetary awards that are tripled for willful violations under 35 U.S.C. § 284, and recent jury verdicts in IP cases have reached hundreds of millions of dollars.
Proprietary information operates differently. It encompasses confidential business information that is valuable to a company but not protected by IP laws—anything from customer lists and pricing strategies to manufacturing processes or internal software tools. Proprietary information derives its value from secrecy; if the information becomes public or known to competitors, it loses the edge it provides.
Here’s how they compare in practice:
| Aspect | Intellectual Property | Proprietary Information |
| Legal Protection | Automatic statutory protection (patent, copyright, trademark laws) | Contractual agreements and state trade secret laws |
| Registration | Often requires formal filing (e.g., patent, trademark registration) | No formal registration needed (must remain secret) |
| Duration | Fixed terms (e.g., 20 years for patents, life + 70 years for copyrights) | Indefinite (lasts as long as secrecy is preserved) |
| Enforcement | Enforced via federal courts and agencies | Enforced via contracts (NDAs, employment agreements) and state courts |
| Disclosure | Requires public disclosure (patents must publish details) | Must remain confidential; disclosure destroys protection |
| Transferability | Treated as property—can be sold or licensed | Limited transfer (sharing usually only under NDA) |
The practical implication: A patent or copyright gives you a right against the world (a competitor independently inventing your patented tech still infringes). Still, a piece of proprietary know-how only retains value as long as others don’t figure it out. Such rights are critical for preventing disputes and maintaining control over valuable assets, ensuring that property rights and intellectual property rights are clearly defined and enforceable.
What Is Intellectual Property?
Intellectual property represents a legal framework for protecting creations of the mind, including inventions, works of authorship, brand identifiers, and proprietary designs. IP law incentivizes innovation and creativity by giving creators defined periods of exclusive rights to profit from their work.
Intellectual property law protects original works, including literary, artistic, and inventive creations. It may also address other intellectual property developed outside the scope of employment or prior to joining an organization.
Patents: Protection for Inventions
In the U.S., a utility patent grants its owner the exclusive right to make, use, or sell the invention for 20 years from the date of application, in exchange for publicly disclosing the invention’s working principles. To be patentable, an invention must be new, non-obvious, and useful.
The scale of patent activity is substantial: the USPTO granted 374,000+ patents in 2022 alone, reflecting the rapid pace of innovation. Pharmaceutical firms patent new drug compounds so competitors cannot copy them during the patent term, while tech companies build extensive portfolios—Microsoft holds over 33,000 patent families globally as of 2023. Securing a patent for a new invention is essential to obtain exclusive rights and prevent competitors from copying innovative products.
For SaaS and software companies, patents protect the technical innovations underlying your platform—whether that’s a novel algorithm, a unique data processing method, or an innovative user interface feature. Unlike copyright (which only protects specific code), patents protect the underlying functionality itself. This means even if a competitor writes entirely different code, if they implement your patented method, they’re infringing. Understanding what makes software patentable is crucial for any tech founder seeking to build a defensible IP portfolio.
Trademarks: Brand Protection
Trademarks safeguard brand names, logos, and other identifiers that distinguish a company’s goods or services. Trademark protection can last indefinitely (with renewals), unlike other IP, as long as the mark remains in use and continues to signify the source of products.
Service marks, like trademarks, protect the branding of services. Both trademarks and service marks can also apply to names and symbols associated with computer programs.
U.S. law allows trademark owners to recover attorney’s fees and treble damages in cases of willful, malicious infringement. The Apple logo and Nike’s “Just Do It” slogan exemplify trademarks that instantly identify their companies’ offerings.
For SaaS founders, your product name and company brand are often among your most valuable assets when raising funding or preparing for acquisition. Strong intellectual property protection not only prevents copycats but also builds brand equity that directly translates to higher valuation multiples.
Copyrights: Creative Work Protection
Copyrights protect original creative works, including literature, software code, music, and art. A copyright arises automatically upon creation of an original work fixed in a tangible medium. It typically lasts for the life of the author plus 70 years (for corporate works, 95 years from publication or 120 years from creation).
For software companies, copyright is particularly critical. Copyright holders can bring infringement lawsuits in federal court seeking either actual damages or statutory damages, which range up to $150,000 per work for willful infringement.
Here’s what many SaaS founders miss: while copyright protects your specific code, it doesn’t stop competitors from studying what your software does and writing their own code to achieve the same result. That’s why layered protection—combining copyright with patents and trade secrets—creates the strongest defensive position.
To ensure proper legal transfer and protection of creative works, organizations often use a standardized form, such as a copyright assignment agreement, to document the assignment of rights.
Trade Secrets: The Hybrid Category
Trade secrets encompass confidential formulas, practices, designs, or compilations of information that have value due to their non-public nature. Trade secrets are unique among IP categories because they do not require registration—protection is automatic as long as the information is truly secret. The company takes reasonable measures to keep it secret.
Famous examples include the formula for Coca-Cola or Google’s search algorithm. Trade secret protection can last indefinitely (or until the secret is disclosed), making it, in some cases, more enduring than a patent.
Many artificial intelligence companies keep their model weights and training data as trade secrets rather than patenting them to avoid disclosing them to the public. For AI-focused startups, understanding how to protect AI innovations through the right combination of patents and trade secrets is essential—patent the core methodology while keeping training data and fine-tuning techniques confidential. However, if a trade secret is independently discovered or leaks, the owner has no exclusive rights (absent a contractual breach or theft).
The layered approach matters: Microsoft’s Windows operating system exemplifies multi-layered IP protection, featuring thousands of patents on technologies, copyright for the actual source code and software binaries, trademarks for the Windows name and Microsoft brand, and the treatment of the Windows source code as highly proprietary information with restricted access. Proprietary rights over confidential processes and know-how are crucial for maintaining a competitive edge, even when such rights are not formally registered.
What Is Proprietary Information?
Proprietary information refers to confidential business information that derives its value from being secret. It’s the broad universe of data, knowledge, and know-how that a company develops internally and that gives it a competitive edge, but which has not been formally protected by intellectual property laws.
Protecting proprietary information is crucial to prevent unauthorized disclosure, which can result in the loss of competitive advantage and potential misuse of sensitive data.
Unlike registered IP rights, proprietary information does not automatically receive protection under law simply by virtue of its creation. Suppose a company develops a brilliant new manufacturing process but fails to patent it. In that case, the law will not prevent a competitor from using the same process if they discover or reverse-engineer it.
Categories of Proprietary Information
Customer and Sales Data: Customer lists, contact information, purchase histories, pricing terms. Companies like Salesforce or Oracle invest heavily in curated customer data; these databases are invaluable for sales and marketing strategy and are kept tightly guarded, since a competitor with that data could directly target your clients.
Internal Business Processes: Specialized manufacturing processes, quality control procedures, or logistical systems that a company has honed over the years. These might not rise to the level of patentable inventions, but they can make the business more efficient or effective. Manufacturing firms often have proprietary process know-how on assembly techniques or sourcing that they consider trade secrets.
Technical Know-How: Source code, software architectures, product designs, experimental research data. In software and SaaS companies, the source code is often proprietary; even if specific algorithms could be patented, many companies choose not to disclose them in patents and instead rely on secrecy.
For SaaS companies specifically, your proprietary information likely includes your database schema, API integration methods, deployment configurations, customer usage analytics, and product roadmap. While you might patent novel features, the operational knowledge of how you built, scaled, and optimized your platform remains a trade secret.
Business Strategies: A startup’s roadmap, marketing strategies, merger and acquisition targets, or pricing strategies. If a competitor knew your 2-year product roadmap or your plan to expand into a new market, they could preempt you.
Financial Information: Proprietary information includes sensitive financial data, such as internal financial analyses, cost structures, and profit margins by product. For example, an e-commerce company’s proprietary data might include a detailed breakdown of customer acquisition costs and lifetime values by channel.
Supplier and Partner Data: Key supplier contacts, terms of supplier contracts, or exclusive distribution arrangements. Many companies treat their supply chain relationships as proprietary to prevent competitors from copying their sources or gaining access to them.
The Legal Framework
The Uniform Trade Secrets Act (UTSA)—a law adopted by 48 U.S. states—defines trade secrets broadly to include all kinds of information that has economic value because it is not generally known and is subject to reasonable efforts to maintain secrecy.
Real-world impact is significant. When employees with knowledge of OpenAI’s GPT-4 secrets left for competitors, it led to legal disputes, including when Elon Musk’s startup xAI accused OpenAI of poaching staff to obtain xAI’s proprietary AI technology details. McDonald’s treats its Big Mac sauce recipe and French fry preparation method as trade secrets, and also maintains extensive proprietary manuals for franchisees, which are shared only under confidentiality within the franchise system. An organization must implement NDAs and confidentiality agreements to protect sensitive information shared within its operations.
Legal Protection Mechanisms
The enforcement pathways for intellectual property versus proprietary information operate through fundamentally different legal systems, each with distinct advantages and limitations. Adequate intellectual property protection requires both legal strategies and internal measures to protect intellectual property from loss or misuse.
Intellectual Property: Statutory Rights
Patent Enforcement: If someone uses your patented invention without permission, you can sue for patent infringement in federal court. Remedies include injunctive relief (a court order stopping the infringer) and monetary damages—often calculated as lost profits or a reasonable royalty. In cases of willful infringement, courts can award up to three times the damages as punishment. If you need guidance on patent enforcement, consider consulting a registered patent attorney for professional advice.
U.S. courts have seen patent verdicts ranging from tens of millions to over $1 billion in recent years (though significant awards may be reduced on appeal).
Trademark Enforcement: Trademark owners can file civil suits under the Lanham Act for trademark infringement or dilution. U.S. law allows trademark owners to recover attorney’s fees and treble damages in cases of willful, malicious infringement.
Copyright Enforcement: Copyright holders can bring infringement lawsuits in federal court seeking either actual damages (including profits the infringer made) or statutory damages, which range up to $150,000 per work for willful infringement.
Proprietary Information: Contracts and Trade Secret Law
Contractual Agreements: Non-disclosure agreements (NDAs) and confidentiality clauses in employment contracts create a contractual duty for recipients of confidential info not to disclose or misuse it. Consulting agreements often include confidentiality and assignment clauses to ensure that such information, including proprietary data and inventions, is adequately protected and assigned to the company. If someone signs an NDA and then leaks your proprietary data, you can sue them for breach of contract.
Trade Secret Law: The Uniform Trade Secrets Act (UTSA), adopted by most states, and the federal Defend Trade Secrets Act (DTSA) of 2016 allow companies to sue for theft or misuse of trade secrets. To qualify, the information must be secret, valuable due to its secrecy, and subject to reasonable efforts to maintain secrecy.
The Economic Espionage Act of 1996 makes theft of trade secrets a federal crime, with fines up to $5 million for companies and 10 years’ imprisonment for individuals.
The enforcement statistics are striking: Over 80% of trade secret cases that go to judgment favor the plaintiff (the trade secret owner), and courts have shown willingness to award massive damages in severe cases (including jury awards over $500 million in some recent trade secret trials).
Critical Jurisdictional Differences
The Defend Trade Secrets Act (DTSA) of 2016 created a federal civil cause of action for trade secret theft, allowing companies to sue in federal court even if diversity jurisdiction doesn’t exist. DTSA also introduced a provision for ex parte seizure, allowing a court to order the seizure of property (such as a laptop or server) to prevent the dissemination of a stolen trade secret in exceptional circumstances.
Patent, copyright, and trademark cases are exclusively federal matters. In contrast, trade secret cases can be brought in either state court or federal court, depending on the applicable law (such as the DTSA or diversity jurisdiction).
One crucial limitation: Courts will ask whether you marked documents as confidential, stored them securely, restricted access, and trained employees on secrecy. Failing to take such steps can undermine both contract and trademark claims. Cases have been lost because a company failed to have employees sign NDAs or didn’t prove that it attempted to keep the information secret.
Protection Strategies and Best Practices
Adequate asset protection requires systematic implementation across multiple organizational layers, moving beyond simple paperwork to comprehensive operational integration.
1. Asset Identification and Classification
Take inventory of your intangible assets. Which innovations are patentable? Which brand elements need trademarking? Which information is sensitive and should be kept confidential? Create an IP registry (for patents, trademarks, copyrights you own) and a confidential information registry or classification scheme.
Many firms use a tiered classification system, including Public, Internal, Confidential, and Highly Confidential. This determines handling requirements for each asset type.
For SaaS founders preparing for fundraising, this audit becomes especially critical. VCs increasingly scrutinize IP ownership and protection as part of due diligence. Having proper legal documentation that clearly establishes your ownership of all IP assets—including invention assignments from founders and contractors—can make or break a deal.
2. Formal IP Protection
If you have a novel invention or design that is core to your business advantage, strongly consider filing for a patent (or at least a provisional patent application to secure a filing date). Patents are especially critical in industries such as biotech, pharmaceuticals, and manufacturing, where reverse engineering is feasible and long-term exclusivity is desired. In some cases, protecting your innovations as trade secrets may also be an effective part of your intellectual property strategy.
Register trademarks for your brand names, logos, and product names in all key markets you operate. For creative content or software, register copyrights for important works—registration in the U.S. is needed to seek statutory damages in litigation.
3. Comprehensive Confidentiality Programs
Clear Policies: Have a written policy (often outlined in the employee handbook or code of conduct) that defines what your company considers confidential and how it must be handled. Ensure that employees understand that client data, source code, business plans, and other confidential information are proprietary and protected.
Access Controls: Follow the principle of least privilege—give access to sensitive information only on a need-to-know basis. Use IT controls (permissions, encryption, VPN for remote access) to secure digital data. Physically, keep servers in secure rooms, use badge access for labs, and mark confidential files as such.
Employee Training: Regularly train employees on their responsibilities regarding confidentiality. New hires should get training as part of onboarding (and sign an acknowledgment). Provide refreshers annually or when specific issues arise.
Third-Party Handling: Before sharing sensitive info with any outside party, have an NDA in place. And only share what’s necessary—if a marketing agency is helping with a campaign, they might not need access to product source code or financials unrelated to their task.
4. Strategic Contractual Protection
Non-Disclosure Agreements: A good NDA defines what information is confidential, the permitted purpose of disclosure, and prohibits the recipient from using it for any other purpose or sharing it further. It should also require them to return or destroy the info upon request or at project end.
Employment Agreements: Ensure that every employee signs an agreement with confidentiality clauses and an IP assignment clause. The agreement should stipulate that during and after employment, the individual must not use or disclose the company’s confidential information, except for the benefit of the company. It should also clarify that any inventions or works created in the scope of their job belong to the company.
For key technical employees, some companies also include non-compete clauses or non-solicitation clauses—though enforceability varies by state and recent legal trends.
Contractor and Partner Agreements: A software contractor’s agreement should state that all code they write for you is owned by your company (work-for-hire or assignment clause) and that they will treat any access to your systems/data as confidential. Businesses may also use a license agreement to permit third parties to use intellectual property under specific terms and conditions, helping to control rights and establish enforceable terms for long-term partnerships.
5. Technology-Based Prevention
Consider using Data Loss Prevention (DLP) software, which can detect and block sensitive data from being emailed out or uploaded to unauthorized cloud storage. For highly sensitive files, use digital rights management (DRM) or at least password protection. Monitor unusual access patterns.
6. Patent vs. Trade Secret Decision Framework
Sometimes you have a choice: patent it or keep it secret? Patenting provides strong protection but discloses the invention publicly (after 18 months, patent applications are made public). If the invention can be easily reverse-engineered once a product is released, patenting may be the only way to protect it.
Google did not patent the full details of its search algorithm—it relied on secrecy, considering the algorithm continually evolves and is difficult to infer from outside results. On the other hand, pharmaceutical companies generally patent drug formulas because once the drug is sold, anyone can analyze its composition and potentially replicate it.
For AI and machine learning innovations, the decision often comes down to this: patent the novel algorithmic approach or system architecture (the “how”), but keep training data, model weights, and specific implementation optimizations as trade secrets. This gives you both offensive patent rights and defensive trade secret protection.
7. Regular Audits and Updates
Conduct periodic audits—inventory new innovations or content that may require IP filings, verify that trademarks are renewed and used correctly, and review who has access to what confidential information internally. As your business evolves, update your protection measures.
Practical Applications Across Industries
Technology: Microsoft’s Layered Strategy
Microsoft’s Windows operating system exemplifies sophisticated protection combining multiple mechanisms. The company holds thousands of patents covering technologies related to Windows (over 33,000 patent families globally). It also uses copyright to protect the actual Windows source code and software binaries, and trademarks to protect the Windows name and the Microsoft brand.
At the same time, Microsoft treats the source code for Windows as highly proprietary information, restricting access to it and requiring confidentiality even from partners—ensuring that, beyond the public-facing IP rights, the implementation details remain secret to prevent outright cloning.
Pharmaceuticals: Dual Protection Approach
Big pharma relies on patents to protect new drugs (since once a drug’s formula is known, any chemist can make it). However, pharmaceutical companies also generate vast amounts of proprietary data that is not covered by the patent, such as the detailed manufacturing process for the drug, the analytical methods used to test quality, and the results of clinical trials.
When a pharma firm patented a new biologic drug, it kept the specific cell line and cultivation process as trade secrets (since those can be hard to replicate even if you know the formula).
The enforcement is real: A GlaxoSmithKline scientist was convicted of stealing confidential data on cancer drugs to send to a China-backed startup. GSK had robust internal controls, but this case highlighted that insider threats are a genuine concern.
Manufacturing: Tesla’s AI Protection
In 2022, Tesla sued a former engineer for downloading confidential files about its AI training supercomputer (Dojo) and Autopilot source code—an explicit trade secret enforcement action. That case was settled in 2023, with the engineer admitting to transferring confidential data and paying a settlement.
What Tesla did right: they had robust internal monitoring that detected the unusual data downloads, strong employment agreements, and they moved quickly to litigate, sending a clear message that such misappropriation would not be tolerated.
Fast Food: McDonald’s Franchise Model
McDonald’s utilizes trade secret law to protect its recipes (the Big Mac sauce being a classic example) and maintains the confidentiality of its operations manual, which is provided to franchise owners. The franchise agreement contains strict clauses: the franchisee is permitted to use the proprietary methods solely for operating the franchised restaurant and must not disclose them to anyone.
Common Misconceptions That Cost Companies Millions
Misconception 1: Automatic Protection for Valuable Information
Many business owners assume all critical information is somehow legally protected. You cannot patent a list of customers or a pricing strategy; you cannot copyright an idea for a mobile app (only the code or specific expression when created). These fall under proprietary information, which means you only have protection if you keep them secret and contractually restrict access to them.
A classic scenario: a startup pitches an idea (without an NDA) to an investor or partner, who then implements it. Unless there was a specific legal protection (such as a patent pending or an NDA in place), the idea itself wasn’t owned.
Misconception 2: All Proprietary Information Qualifies as Trade Secrets
Not all proprietary info qualifies as a trade secret in court. The law sets thresholds: the information should have independent economic value, separate from its general knowledge, and you must use reasonable efforts to maintain secrecy.
Courts have denied trade secret claims when a company didn’t require employees to sign confidentiality agreements or left a supposedly secret process accessible to many people without adequate controls.
Misconception 3: Contracts Alone Provide Complete Protection
A signed NDA won’t physically stop someone determined to steal or leak information. It only gives you grounds to sue after the fact. If you have all employees sign NDAs but then never train them on handling secrets, or you leave your server with sensitive data unencrypted, you’re inviting trouble.
Ensure NDAs cover use of information, not just disclosure, to avoid gaps where someone claims “we kept your info confidential, we just independently developed similar.”
Misconception 4: One-Time Protection Is Sufficient
IP management and information security are ongoing processes. You need to update IP filings as you improve products, maintain those IP rights (pay maintenance fees for patents, renew trademarks, police for infringement), and adapt to new threats.
Critical Action Steps to Avoid These Pitfalls
Audit IP and proprietary assets regularly. Maintain rigorous confidentiality programs with documentation of efforts (so you can demonstrate “reasonable efforts” if needed in court). File for formal IP rights promptly for key innovations (before public disclosure or employee departure loses the chance).
Be mindful of departing employees—conduct exit interviews and ensure they haven’t taken any sensitive data. Some companies conduct forensic inspections on devices when high-level engineers or executives leave—this can deter theft and catch it if it occurs.
Recent Legal Developments (2022-2025)
Surge in Enforcement and Litigation
The landscape has shifted dramatically. U.S. officials estimate that theft of intellectual property costs the U.S. economy between $225 billion and $600 billion annually. A significant portion is attributed to economic espionage by nation-states.
FBI Director Christopher Wray remarked in 2022 that “there is just no country that presents a broader threat to our ideas, our innovation, and our economic security than China,” noting that FBI counterintelligence operations for Chinese economic espionage open new cases roughly every 12 hours.
The Department of Justice reports that cases initiated for IP theft increased by 21%, criminal arrests rose by 39%, indictments increased by 99%, and convictions rose by 29% compared to the prior year.
Jury awards reflect the severity of the case: In May 2022, a Virginia state court jury awarded $2.0 billion in damages in a trade secret case between Appian Corp. and Pegasystems. Between 2019 and 2023, at least five U.S. trade secret cases resulted in awards exceeding $100 million.
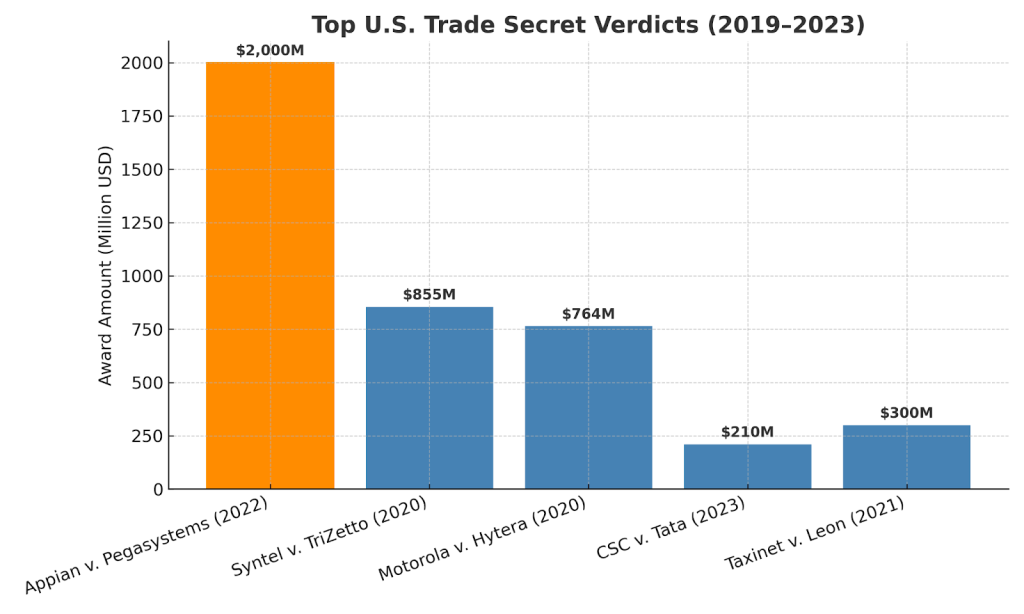
Figure 1: Top Major U.S. trade secret verdicts from 2019–2023 illustrate the soaring financial stakes of proprietary information theft. Jury awards exceeding $100 million were recorded in at least five cases during this period—source: Kirkland & Ellis.
Trade secret litigation has increased by ~30% since the passage of DTSA in 2016, and over 1,100 federal trade secret cases were filed in 2022 alone.
New Sanctions Authority
A significant new law, the Protecting American Intellectual Property Act of 2022 (PAIPA), was enacted in January 2023. This law requires the U.S. government to identify and sanction foreign individuals and companies involved in significant theft of U.S. trade secrets. The sanctions can include freezing assets and cutting off access to U.S. markets.
The Biden Administration in 2024 delegated authority to the State and Treasury Departments to implement these sanctions, signaling that the U.S. is gearing up to use economic penalties as leverage against large-scale IP thieves.
Non-Compete Agreement Restrictions
In April 2024, the Federal Trade Commission finalized a rule to ban virtually all non-compete clauses in employment contracts. This sweeping rule (if it comes into effect after ongoing legal challenges) would invalidate an estimated 30 million existing non-competes nationwide.
The FTC argues that trade secrets and confidential information can be protected by narrower means like NDAs, non-solicitation agreements, and trade secret lawsuits rather than blanket employment restrictions.
Companies may soon lose non-compete agreements as a tool and will need to rely even more heavily on trade secret law and robust confidentiality practices. Executives should review their agreements in light of these changes and consider enhancing other protections—such as ensuring they have robust NDAs that cover post-employment confidentiality.
AI and Patent Eligibility
Courts and the USPTO have affirmed that AI systems cannot be inventors on patents—a 2022 Federal Circuit ruling held that under current law, an inventor must be a natural person. This underscores the importance of companies using AI to generate inventions with human researchers listed as inventors.
This development has significant implications for AI startups and SaaS companies building AI-powered features. While your AI model can help discover novel solutions, you need human inventors on record for any patent applications. The good news? This legal framework actually protects you—it means competitors can’t simply have their AI generate thousands of patents to create defensive barriers.
Your Next Steps to IP Protection Success
If you’re a founder or inventor reading this, you’ve just absorbed a lot of complex information. Here’s what matters most: understanding the difference between proprietary information and intellectual property isn’t just legal theory—it’s the foundation of protecting what makes your business valuable.
The bottom line: Weak IP protection invites competitors to clone your innovations. Strong, layered IP protection—combining patents, trademarks, trade secrets, and airtight contracts—creates real barriers that deter infringement and give you leverage in negotiations, fundraising, and eventual exits.
Currently, with IP theft cases surging and trade secret litigation increasing by 30% since 2016, hesitation costs you a competitive advantage. Every day without proper protection is a day competitors could be reverse-engineering your product, poaching your employees with proprietary knowledge, or filing patents on improvements to ideas you shared carelessly. Under the U.S. first-to-file system, whoever gets to the USPTO first wins—even if you invented it first.
Here’s what you need to do immediately:
- Schedule a Free IP Strategy Call with our team to evaluate your specific innovations and develop a comprehensive protection plan covering patents, trade secrets, trademarks, and employment agreements.
- Audit your current IP position: Document what you’ve invented, what you’ve disclosed publicly, who has access to trade secrets, and whether proper contracts are in place.
- Identify your crown jewels: Determine which innovations are core to your competitive advantage and require immediate patent protection versus those that can remain as trade secrets.
- Review and update all agreements: Ensure every employee, contractor, and partner has signed proper NDAs and invention assignment agreements that actually protect you.
- Consider a professional Patentability Search: Before investing in patent prosecution, understand whether your invention is truly novel and worth pursuing. The Patentability Search is the gateway to the patent process—it reveals whether prior art threatens your innovation and helps you make informed decisions about protection strategy.
The RLG Guarantee: Risk-Free Patentability Assessment
We’re so confident in our patentability search process that we back it with The RLG Guarantee: If we conduct the patentability search and find that your invention is not novel, we’ll issue a 100% refund.
This guarantee means you can pursue IP clarity without financial risk. You’ll receive:
- Invention discovery call with your attorney to gather comprehensive search information
- Comprehensive patentability search covering U.S. and foreign patents plus published applications
- Detailed patentability report reviewing findings and outlining IP protection strategy options
- Attorney review call to discuss search results and next steps for your innovation
- 100% refund if the search conclusively shows your invention lacks novelty
Learn more about The RLG Guarantee and how it removes risk from your IP protection journey.
The competitive advantage you’ve built isn’t safe until it’s protected. Your IP portfolio isn’t an expense—it’s an investment in defensibility, valuation, and long-term competitive positioning. Companies with strong IP protection command higher valuations, attract better investors, and survive competitive pressures that sink under-protected rivals.
The companies dominating your industry five years from now won’t just be the ones with the best technology—they’ll be the ones who protected that technology adequately before competitors could copy it.
Schedule your Free IP Strategy Call today to start building the layered protection your innovations deserve.
About the Author
Andrew Rapacke is Managing Partner and a Registered Patent Attorney at Rapacke Law Group, where he specializes in helping tech startups and SaaS companies protect their innovations through strategic IP planning. With deep expertise in software patents, AI protection strategies, and trade secret enforcement, Andrew collaborates with founders to develop robust IP portfolios that support fundraising, scaling, and successful exits.Connect with me: LinkedIn: Andrew Rapacke | @rapackelaw on Twitter/X | @rapackelaw on Instagram




