In 2018, a Waymo engineer walked out with thousands of confidential files containing critical self-driving car source code and took them to Uber. The theft cost Uber $245 million in stock to settle. More recently, a former Google engineer was arrested for stealing AI-related trade secrets to benefit companies in China. These aren’t isolated incidents; trade secret theft now costs the U.S. economy between $180 billion and $540 billion annually, with the Computer Software & Services industry seeing the most trade secret case filings of any sector in 2025.
For SaaS businesses, your source code isn’t just intellectual property: it’s your competitive advantage, your “secret sauce” that customers pay for. When competitors reverse-engineer proprietary features, or employees exfiltrate them, they’re stealing years of development work and millions in potential revenue. The threat is escalating: according to Verizon’s 2024 Data Breach Investigations Report, 60% of data breaches involve a human element (errors or insider misuse), and breaches that expose intellectual property are the most costly, averaging $178 per record.
But here’s what most SaaS founders miss: protecting your source code is only half the battle. Copyright protects the literal expression of your code, the specific way you wrote it. A sophisticated competitor can reverse-engineer your features, understand the underlying logic, and rewrite their own implementation from scratch. No copyright infringement. No legal recourse. Your “secret sauce” is now their feature. This is why software patents matter. They protect the functionality itself, the novel method or process your software uses, regardless of how the code is written. Without patent protection, all the security measures in the world won’t stop a determined competitor from legally replicating what makes your software valuable.
This article explores five research-backed measures to stop competitors from stealing your software features and prevent employees from misappropriating source code. These strategies combine legal protections, technical safeguards, and organizational practices, with a critical emphasis on why patents, not just code security, are your primary defense against competitive threats.
How to Prevent Employees from Stealing Source Code: Introduction to Code Security
Your source code represents years of development work and millions in potential revenue. Yet most SaaS companies treat code security as an afterthought, until a former employee walks out with their competitive advantage. Code security isn’t just about protecting intellectual property; it’s about maintaining the competitive edge that customers pay for.
However, it’s essential to understand what code security can and cannot protect. Security measures guard against theft of your source code, prevent employees from copying files, block unauthorized access, and detect exfiltration attempts. What they cannot stop is the replication of your functionality. A competitor who never touches your source code can still study your software’s behavior, reverse-engineer the underlying logic, and build their own clean-room implementation. This is perfectly legal, and no amount of encryption or access controls will stop it.
This distinction matters because it determines where you should focus your protection efforts. Adequate code security requires robust access controls, continuous monitoring, and proactive threat detection to prevent source code theft and malicious code insertion. These measures are critical given the current threat landscape: 60% of data breaches involve a human element (errors or insider misuse), and breaches that expose intellectual property are the most costly, averaging $178 per record.
But the most critical protection (the one that survives reverse-engineering) is patent protection for your novel functionality. By prioritizing both patent protection for your innovations and code security throughout the software development lifecycle, you protect your competitive advantage, maintain customer trust, and avoid costly security incidents that can derail your business. In today’s digital landscape, where trade secret theft costs the U.S. economy up to $540 billion annually, investing in comprehensive IP protection isn’t just a technical necessity; it’s a business imperative.
1. Understand What Makes Your Software Unique
What features or combination of features and functionality on your SaaS platform are genuinely unique and most likely to be targeted by competitors? Answering this question effectively can help you avoid wasted time and effort spent blocking competitors from copying aspects of your software that may not be protectable or are trivial.
Many developers overlook the importance of identifying and protecting these unique aspects until they encounter copycats. If a novel feature is popular and a key reason why customers pay for your software, then it deserves further investigation and protection. Consider keeping a running list or chart of these critical features as a handy reference when determining if competitors may be using your proprietary modules or processes. Integrating secure coding practices, such as avoiding hardcoded secrets and following secure coding standards, can further safeguard these critical components.
The Legal Significance of Identifying Your Secret Sauce
Identifying your “secret sauce” is not just an internal exercise: it has legal significance. Under U.S. trade secret law, only information that companies actively keep secret and valuable can be protected as a trade secret. This means documenting the features and implementing safeguards around them.
Once you’ve identified these core innovations, the critical question is whether they are patentable. Features that represent novel, non-obvious methods of solving problems are prime candidates for utility patents, unlike trade secret protection (which evaporates the moment a competitor figures out how your software works), patent protection remains enforceable regardless of whether the innovation becomes publicly known. A competitor can study your product, understand precisely how your feature works, and still be liable for patent infringement if they implement the same method.
By knowing precisely what gives your software its competitive edge, you can focus security efforts and legal protections on those areas. This proactive approach is vital because competitors often target the most valuable, differentiated features of a successful product.
High-profile corporate espionage cases underscore this risk. The Waymo-Uber dispute, in which an ex-employee allegedly stole thousands of confidential files, including critical source code, resulted in a $245 million settlement. This example shows how much value can be tied up in a single company’s unique technology.
By clearly pinpointing what makes your software unique (and keeping that information well-secured), you put yourself in the best position to guard against such theft and to take swift action if it occurs.
2. Keep a Close Eye on Your Competition
Understanding your competitive landscape isn’t optional; it’s essential for protecting your innovations. Before you can monitor competitors effectively, you must first identify who they are and what threats they pose to your market position.
When analyzing competitor products, it’s essential to review any open source code components they use. Automated code-scanning tools can quickly identify vulnerabilities in open-source components that manual reviews might miss due to their complexity or volume.
Identifying Your Competitors
SaaS businesses may have both direct and indirect competitors, from similarly situated companies offering a narrow set of competing services to companies that don’t provide the same services but compete in adjacent ways. Start by performing general market research and leveraging tools like search engines, SaaS review sites, product review sites, and social media to identify companies offering similar solutions (e.g., searching for “best [your type of product] software”). Look for businesses in the same geographic or tech “hotbed” areas, and search for terms such as “top” or “most popular” [product category] to identify potential rivals.
Monitoring Competitor Features
Once competitors have been identified, perform in-depth analyses of their product offerings. Informal methods of determining what features competitors have include:
- Monitoring their marketing materials and website updates.
- Purchasing a subscription to their platform to experience it firsthand.
- Following their social media and promotional campaigns.
- Listening to feedback from your own clients or prospects who mention competitor features.
Formal methods can involve researching public records: for example, searching the U.S. Patent and Trademark Office (USPTO) database for published patents or pending applications by those competitors, looking up trademark filings, and even checking international patent databases if you suspect they operate globally. (Keep in mind there is usually an 18-month lag between a patent application’s filing and its publication, but savvy analysis of patent trends can still provide clues to competitors’ R&D focus.)
By combining informal and formal investigative methods, SaaS businesses can often determine whether competitors are moving into their space or have copied/stolen a valuable innovation. Forward-thinking SaaS companies even compile a “competitor watch” document and update it periodically to track how rivals’ offerings evolve.
Why Vigilance Matters
Staying vigilant about competitors’ feature sets is critical because feature-copying is a common tactic in the tech industry. Instagram famously copied the entire “Stories” feature from Snapchat in 2016 (even retaining the same name), a move that helped Instagram attract hundreds of millions of users and slowed Snapchat’s growth. This kind of fast-follow imitation can quickly erode your competitive advantage if you’re caught off guard.
Monitoring competitors’ products and updates helps ensure you’re aware when they introduce something that appears to copy your unique features. When you do detect a competitor launching a feature that you pioneered, you can investigate how they developed it: whether it’s merely a coincidence, legitimate independent development, or possibly the result of leaked information or a former employee’s knowledge.
The Rising Threat of IP Theft
Companies are increasingly willing to take legal action in such scenarios: the number of trade secret theft lawsuits remains high, with hundreds of cases filed each year in U.S. courts. Software and technology companies lead in these disputes, reflecting how frequently tech firms clash over copied features or stolen code.
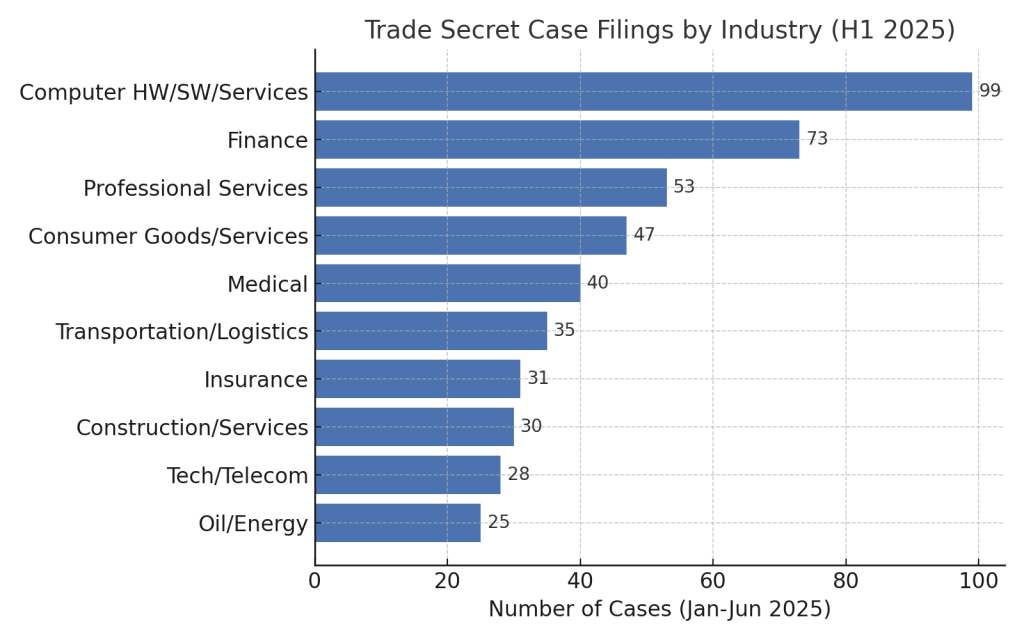
Figure 1: Trade Secret Case Filings by Industry Sector (H1 2025): Computer Software & Services leads with 99 new cases, demonstrating the intense IP protection landscape in tech. Source: CRA Trade Secret Litigation Watch
This indicates intense competitive pressures in the software space.
By keeping a close eye on your competition’s moves and maintaining evidence of your own innovations, you’ll be prepared to act if a competitor too closely mimics your software’s key features.
3. File for Intellectual Property Protection for Your Software
Filing for formal intellectual property (IP) protection for your SaaS company’s software can be one of the most effective ways to prevent competitors from stealing your valuable features. All major types of IP protection can apply to software in different ways:
- Utility patents can protect functional aspects and novel technical features of your software (e.g., a unique algorithm or process).
- Design patents can protect aesthetic aspects, such as the appearance of a user interface or graphical elements.
- Copyright automatically protects the source code (as a literary work) and other creative elements (such as documentation or UI graphics) the moment they are created. However, registering the copyright provides additional legal benefits.
- Trademarks protect your source-identifying names, logos, and taglines that distinguish your software or company in the marketplace.
Why Patents Protect What Copyright Cannot
Many SaaS founders believe that keeping their source code secret and protected by copyright is sufficient. It’s not. Here’s why:
Copyright protects the expression of your code, the specific syntax, structure, and organization you wrote. It does not protect the underlying functionality, algorithms, or methods your software implements. This creates a critical vulnerability: a competitor can legally analyze your software’s behavior, understand what it does and how it works, and then write their own code to achieve the same result. Different code, same functionality. Zero copyright infringement.
Software patents close this gap. A utility patent protects the functional method or process your software performs, regardless of how the code implementing it is written. If you’ve patented your novel approach to client intake automation, lead scoring, document analysis, or any other functional innovation, a competitor infringes that patent whether they copy your code directly or write entirely new code that performs the same function.
Consider the distinction:
- Copyright scenario: A competitor reverse-engineers your feature and rewrites it in a different language or architecture—result: No infringement, no recourse.
- Patent scenario: A competitor implements the same functional method you patented, using entirely different code—result: Patent infringement, injunction, and damages available.
This is why the most sophisticated tech companies treat patents (not source code security) as their primary competitive moat. Apple, Google, Microsoft, and Amazon spend billions on patent portfolios not because they’re worried about literal code theft, but because they understand that functionality is what matters competitively. The security measures outlined later in this article are essential for protecting trade secrets and preventing direct code theft. But they cannot stop a determined competitor from replicating your functionality through clean-room development. Only patents can do that.
The Power of “Patent Pending”
While obtaining issued patents, registered copyrights, or trademarks provides the strongest protection, even filing applications for these rights can confer benefits. For instance, after filing a provisional or non-provisional patent application, your SaaS business can mark the pertinent features as “patent pending.”
This puts the world on notice that you have sought protection and that copying the marked features could lead to legal consequences once the patent is granted. Simply adding “patent pending” to a feature can deter would-be infringers by signaling that they could face an infringement lawsuit.
Similarly, filing a trademark application allows you to use “™” (and once registered, “®”), warning competitors that your brand identifiers are legally protected.
Software Patents Are the Norm
Importantly, software-related IP filings are extremely common, indicating that competitors are likely protecting their innovations as well. The USPTO awarded over 325,000 utility patents in 2022, and, notably, 63.5% of those were “software-related,” covering software or computer-implemented inventions.
Software patents now account for the majority of all patents, underscoring the critical role of software innovation across industries. This also means that if you do not patent your software innovations, your competitors may patent their versions and use those patents against you. In a first-to-file system, the first filer prevails, regardless of who actually invented first.
Legal Recourse and Defensive Protection
Owning IP rights gives you leverage: you can license your technology, pursue infringers, or use patents defensively to counterclaim if a competitor sues you. Beyond patents, a registered copyright for your code can facilitate takedowns (e.g., you can send DMCA notices if someone posts your code publicly without permission), and trademarks help you combat copycats that mimic your branding or UI look and feel.
Finally, securing IP rights provides legal recourse if your software features are stolen or misappropriated. If a competitor blatantly copies your patented feature, you can sue for patent infringement (with potential injunctions and damages). If a former employee leaks your source code, you can invoke copyright and trade secret laws (including the federal Defend Trade Secrets Act of 2016) to seek remedies.
Marking your innovations with IP notices (patent pending, ©, ™/®) and actually obtaining those rights builds a legal moat around your software. These steps significantly raise the stakes for any competitor considering theft or imitation of your key features.
The Bottom Line on Patents vs. Code Security
Think of your protection strategy as having two layers:
- Patents protect functionality: Even if a competitor never sees your code, studies your product legally, and builds their own implementation from scratch, they’re still infringing if they use your patented method.
- Code security protects implementation details: The specific way you’ve written your code, your trade secrets, your proprietary optimizations. These are protected by the security measures in Section 4.
Both layers matter, but patents are the foundation. Without them, code security is like building an elaborate vault to protect something that can be legally photographed and reproduced elsewhere.
4. Lock Down Your Codebase with Proper Security Measures
For many SaaS businesses, the source code is their most valuable proprietary asset: essentially a core trade secret containing sensitive data and confidential logic that must be protected at all costs. Secrets such as API keys, tokens, passwords, encryption keys, database credentials, or proprietary algorithms are often stored in code. If misappropriated or exposed, these could be devastating to a company’s long-term trajectory, enabling competitors or attackers to exploit your systems or duplicate your product. Companies must actively protect their source code from both internal and external threats, as traditional security controls alone are often insufficient.
Important context: The security measures below are critical for protecting trade secrets and preventing direct code exfiltration. However, it’s essential to understand their limitation: these measures safeguard against theft of your code, not replication of your functionality. A competitor who never sees your source code can still study your software’s behavior and build a competing product. That’s why the patent protections discussed in Section 3 are your first line of defense for protecting functionality, while the measures below protect your implementation details and trade secrets.
While cybersecurity measures are essential for protecting source code, a multifaceted strategy offers additional benefits that are often overlooked. On the technical side, there are “hard” security measures; on the administrative side, “soft” measures; both are critical. Controlling access to sensitive code and system components (such as through role-based access control, or RBAC) is essential to prevent unauthorized access and data breaches. Below, we outline several layers of defense you should implement to secure your codebase against both insider threats (e.g., rogue or careless employees) and external attackers.
Implementing Access Controls to Limit Exposure
Implementing robust access controls is a foundational step in protecting your source code from unauthorized access and potential theft. By restricting access to sensitive repositories and systems, you ensure that only authorized personnel can view or modify critical code components.
Use the Principle of Least Privilege: each developer, engineer, or contractor should have only the access they need for their role—no more. Limiting access to source code to approved corporate devices is also a best practice, as it helps prevent employees from copying it on a personal device for later use.
The Principle of Least Privilege restricts developers’ access to only the specific code modules they need for their current tasks. This might mean segmenting your codebase so that teams only access the modules they work on, and using network segmentation to isolate sensitive resources. Role-based access control (RBAC) is a common practice where permissions are tied to defined roles and responsibilities within the organization. It is essential to limit access to sensitive code repositories to only those who require it.
Multi-Factor Authentication Is Essential
Strong authentication mechanisms are a must. Multi-factor authentication (MFA) should be required for any access to code repositories or build systems, making it much harder for malicious actors to compromise accounts. Additionally, integrate identity management tools with your version control system to maintain an audit trail of who accessed or changed code and when.
Modern cloud-based repository platforms (such as GitHub and GitLab) offer fine-grained access controls and logging. Take advantage of these features to monitor access patterns. Regularly review and audit access lists, and promptly revoke credentials when team members leave or no longer need access.
The Access Control Gap
It’s worth noting that many organizations acknowledge the importance of strict access control, but not all follow through. According to a 2024 Insider Threat Report, 93% of organizations reported that strict visibility and access control were necessary. Yet, only 36% had a practical, unified solution in place to monitor and control access across their systems.
Don’t let this gap exist in your company. By proactively managing and limiting access, you significantly reduce the risk of both deliberate insider leaks and accidental exposure of source code.
Use approved corporate devices and secure environments for code work. Some companies implement Virtual Desktop Infrastructure (VDI) or use jump hosts for developers, ensuring code never resides on personal devices and that all development occurs in a contained, monitored environment. While this can cause some inconvenience, it significantly limits the ways code can be copied or exfiltrated.
In summary, not everyone should have access to all of your source code. And those who do should face multiple barriers (MFA, network restrictions, device management) that protect your crown jewels behind layers of defense.
Secure Source Code Storage: Best Practices
Storing your source code securely is essential to safeguard your intellectual property and prevent unauthorized access. This starts with using a reputable version control system (VCS) or repository platform that offers built-in security features. Protecting sensitive data in code, such as database passwords and other credentials, is critical to preventing data breaches and unauthorized access.
Systems like Git (with cloud services such as GitHub, GitLab, or Bitbucket) are industry standards. Ensure that whichever platform you use, it is configured for security. That means private repositories (no public exposure), branch protections (to prevent unauthorized changes), and encrypted connections for all data in transit. Secure repositories should use private, access-controlled systems with two-factor authentication and audit logs to further enhance protection.
Ideally, enable end-to-end or server-side encryption for repository code at rest. For example, GitHub encrypts data at rest and in transit by default; verify that any self-hosted repository systems you use do the same or support encryption.
Preventing Code Exfiltration
Limiting who can clone or download the entire repository is another consideration; some companies disable cloning outside the corporate network or require VPN access. Blocking unauthorized users from accessing sensitive code is essential to ensure only trusted, verified personnel have repository access. You can also use Data Loss Prevention (DLP) tools integrated with your repositories to flag or block attempts to export large amounts of code.
Continuous monitoring of repository activity is crucial: unusual events, like a single user downloading many repositories or large swaths of code at odd hours, could indicate malicious intent. Monitoring user activity in source code repositories provides insight into how users interact with the system and which files they access most often.
Learning from Real-World Breaches
Real-world breaches have demonstrated the risks of storing unsecured code. Parts of Twitter’s source code were leaked on GitHub in early 2023, apparently by an insider, and remained online until Twitter filed a legal request to have them removed. This incident underscores the importance of controlling where code can be stored or shared. Additionally, remote access poses significant risks, as attackers may exploit malware, Trojans, or system vulnerabilities to gain unauthorized entry and steal sensitive source code.
To prevent such mishaps, disable repository forking or third-party app integrations that aren’t vetted, as those can create unintended copies of your code. Use secrets management tools to ensure that sensitive credentials are not hard-coded and pushed to repositories (a surprisingly common issue). Behavioral monitoring can help detect anomalous activities, such as bulk code downloads or oddly timed code submissions.
In short, treat your private code repositories with the same vigilance you would a production database containing customer data: lock down access, encrypt everything, and continuously monitor for suspicious activity.
Code Reviews: Catching Vulnerabilities Before They Spread
Regular code reviews are a critical component of secure software development, helping to catch both vulnerabilities and unauthorized changes before they can cause damage. By systematically reviewing source code, your team can identify security flaws, such as buffer overflows, SQL injection points, hardcoded passwords, and other weaknesses that malicious actors could exploit. During code reviews, ensure secure coding practices are followed, such as avoiding unsafe patterns (e.g., hard-coded secrets) and adhering to established secure coding standards. Thorough code review processes can catch malicious or rogue code before it is merged.
Code reviews also serve as a check against the introduction of malicious code (whether inserted intentionally by an insider or unintentionally through the use of compromised open-source components). In essence, it’s a quality assurance step for security, not just functionality.
Manual and Automated Reviews
Both manual and automated code reviews should be employed. Manual reviews (developers inspecting each other’s code) are great for catching logical issues and ensuring coding standards. However, manual code reviews can be time-consuming but are valuable for identifying subtle security issues. Automated static application security testing (SAST) tools can scan code for known vulnerability patterns.
Many vulnerabilities that lead to breaches arise from widespread coding errors. For example, input validation failures can lead to critical exploits. Having a second pair of eyes on code via peer review makes it far more likely that such mistakes will be noticed and corrected early. In addition, consider requiring code to be signed off by a tech lead or security engineer for particularly sensitive parts of the system.
Building a Security Culture
Another benefit of rigorous code reviews is fostering a culture of security awareness among developers. When the team knows that security is explicitly part of the definition of “done” for a coding task, they will begin coding with security in mind. Over time, this can prevent vulnerabilities from being introduced in the first place. Clear company policies play a crucial role in guiding secure development and ensuring everyone follows best practices.
Make code review a standard part of your development workflow (e.g., as a required step in pull requests). Not only will you improve code quality and maintainability, but you’ll also reduce the risk of a subtle security flaw slipping through. Many high-profile security incidents have been traced back to a small piece of unchecked code. Regular reviews ensure there are very few “unchecked” pieces of code in your product. If you’re interested in seeing how industry leaders approach software innovation and protection, take a look at recent software patent examples.
This process, combined with unit and integration testing, will help you catch issues early (when they are cheapest to fix) and protect your software from both accidental bugs and intentional malicious inserts. Regular training sessions help ensure everyone understands their responsibilities and the consequences of violating the rules.
Security Audits: Ensuring Ongoing Protection
Conducting regular security audits is essential for maintaining strong source code security over time. A security audit involves a comprehensive review of your systems, code, and processes to identify vulnerabilities and areas for improvement. Audits also help prevent security breaches by uncovering risks before they can be exploited.
This can include manual code audits, automated vulnerability scanning of your code and running applications, infrastructure configuration reviews, and simulated attacks (penetration testing). The goal is to proactively find weaknesses before an attacker or rogue insider does. During audits, it is also essential to review compliance with policies (such as whether developers follow secure coding guidelines and employees adhere to access control policies) to ensure security measures are enforced in practice, not just on paper.
What Audits Uncover
During a security audit, you might discover issues such as outdated third-party libraries in your code (which may contain known exploits), misconfigured servers that expose your code or data, or gaps in your incident response process. For example, an audit might reveal that specific repositories were left accessible to all employees by default, or that developers have been committing secret API keys into code. These are the kinds of flaws that audits bring to light so you can fix them.
Audits should also review policy compliance: Are developers following the secure coding guidelines? Are employees adhering to the access control policies? An audit can catch when policies exist on paper but aren’t enforced in practice.
Making Audits Count
Audits must be ongoing (e.g., at least annually, or more frequently for critical systems), and you must act on their findings. Treat an audit like a doctor’s checkup for your application’s security: the findings are only helpful if you remediate the issues identified.
Over time, regular audits will also demonstrate to stakeholders (and, if needed, to regulators or courts) that you take security seriously and employ “reasonable measures” to safeguard your code. This due diligence can be crucial if you ever need to pursue a trade secret theft case: you’ll be able to show that you consistently audited and protected the secrecy of your code.
In sum, security audits help ensure that your protective measures keep pace with evolving threats and that your codebase remains as secure as you think it is.
Continuous Monitoring for Threats and Breaches
Continuous monitoring is vital for detecting and responding to security threats in real time, before they escalate into full-blown breaches. By implementing real-time monitoring tools, such as Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS), and user behavior analytics, you can continuously monitor access to your source code and development environment. It is essential to implement continuous monitoring of source code repositories to track user activity, detect suspicious behavior, and maintain visibility, thereby helping prevent potential security breaches.
The idea is to have alarms go off or notifications sent as soon as something suspicious occurs: for example, if an engineer suddenly downloads gigabytes of source code at 2 AM, or if someone tries to disable security controls on a code repository, those events should trigger immediate alerts and automated responses. Continuous monitoring enables a fast incident response. The earlier you detect a breach or insider threat, the more contained the damage will be.
Detecting Data Exfiltration
One key aspect to monitor is unauthorized data exfiltration. DLP solutions mentioned earlier can help by blocking or flagging unusual data transfers (like extensive code archives being emailed out or uploaded to personal cloud storage). Attackers may attempt to access sensitive code repositories; it is crucial to monitor for such attempts using access controls, authentication protocols, and multi-factor authentication. Likewise, monitor for suspicious code commits or alterations. If malicious code is introduced, you want to catch it in the next build or, at the latest, in a code review.
Modern version control systems can integrate with monitoring to flag commits that, say, remove large sections of security code or add calls to external IPs.
Time Is Money in Incident Response
Crucially, continuous monitoring enables a fast incident response. The earlier you detect a breach or insider threat, the more contained the damage will be. Statistics show that the longer an incident goes undetected, the more costly it becomes.
According to Ponemon Institute research, companies take an average of 85 days to contain an insider security incident (up from 77 days a couple of years earlier). Incidents that took more than 90 days to contain cost organizations an average of $17.2 million, while those included in under 30 days cost around $11.2 million.
The message is clear: time is money when responding to breaches. Continuous monitoring helps you detect unauthorized access or data leaks as they occur, enabling immediate response and reducing containment time from months to days or even hours.
By maintaining vigilant oversight of your code and systems (using automated tools and a dedicated security team monitoring dashboards), you can stay ahead of both known and emerging threats. This proactive stance dramatically increases your chances of stopping insider theft or external attacks before they cause irreparable harm to your business.
Code Obfuscation and Encryption Techniques
Sometimes protecting sensitive code requires not just keeping it behind locks, but also making the code itself harder to understand or use, even if someone does get a copy. This is where code obfuscation and encryption come into play as additional layers of defense. Source code obfuscation allows developers to scramble code to protect applications from hackers who attempt to reverse-engineer them.
Adopting a zero-trust approach as part of a comprehensive security strategy further strengthens source code protection by ensuring secure file transfer and strict data governance.
What Is Code Obfuscation?
Code obfuscation is a technique that transforms your source or compiled code into a version that is functionally equivalent to the original but much harder for humans to read and interpret. Obfuscators might rename variables and functions to meaningless labels, remove helpful formatting, and insert decoy code.
The idea is that if a malicious insider or competitor exfiltrates your code, they won’t easily glean your secret algorithms or logic because the code is practically illegible. Obfuscation is especially important for software distributed to end users (such as mobile apps or client-side code), where an attacker could otherwise reverse-engineer the binaries or scripts to understand how they work.
Many commercial software vendors routinely obfuscate their distributed code to protect intellectual property.
Important note: While obfuscation makes your code harder to read, it doesn’t prevent a competitor from studying your software’s behavior and building their own implementation. A determined competitor can still observe inputs and outputs, analyze functionality, and create clean-room code that does the same thing. This is why patents (which protect the functional method regardless of code) remain essential even when you employ obfuscation.
Encryption for Maximum Protection
Encryption takes protection a step further by converting code into an unreadable format that can only be decoded with the proper key. Within a company, you might encrypt sensitive portions of your codebase or configuration and decrypt them only at build time or at runtime in memory.
Some organizations store their most valuable code (e.g., proprietary algorithms) on encrypted servers or modules, so developers don’t have direct access; only the build system can decrypt and compile it. Additionally, when transmitting code (e.g., developers pulling code from a repository), ensure transport-level encryption (e.g., HTTPS/SSH) is always used to prevent interception in transit.
Runtime Protections
For SaaS platforms, also consider runtime protections: techniques such as white-box cryptography or secure enclaves can execute code in a way that, even if an outsider gains access to the running environment, makes it extremely hard to extract the code or logic.
These measures can thwart sophisticated attempts to steal your “secret sauce.” By combining code obfuscation (making code hard to reverse-engineer) and encryption (making it inaccessible without keys), you create multiple layers of defense.
In practice, if someone illicitly obtains your code, these techniques can significantly slow them down to the point where it’s not worth their effort to replicate your product. Of course, obfuscation and encryption won’t stop a determined insider with full access to plaintext source code, but they are excellent safeguards against external threats and opportunistic theft.
When used alongside the other controls discussed, these controls contribute to a defense-in-depth strategy that keeps your most sensitive code safe.
Removing Old and Outdated Code
Maintaining a secure codebase means not only writing new secure code but also being vigilant about old code. Legacy code, modules, or functions written years ago, or code that is no longer actively used, can introduce vulnerabilities if left unchecked.
Often, outdated code may rely on older frameworks or libraries that have since become insecure. Or it may contain deprecated encryption methods, hard-coded secrets, or unpatched known bugs. Attackers know to look for these kinds of weaknesses. Thus, it’s essential to regularly review your codebase for obsolete or unused code and remove or refactor it as needed.
The “If You Don’t Need It, Don’t Keep It” Principle
A common mantra in security is “If you don’t need it, don’t keep it.” Unnecessary code not only adds bloat but also increases the attack surface. For example, a web application might have an old debugging interface or an unused API endpoint left in the code. If an attacker discovers it, they could exploit it to get in.
By scrubbing such code, you eliminate those potential entry points. With version control, you can confidently delete code from the main branch, knowing it’s still preserved in history if needed for reference.
The Equifax Warning
Also, pay attention to your third-party dependencies. If you included open-source libraries or plugins years ago and haven’t updated them, they may now have known security vulnerabilities.
One famous example of neglected outdated software causing a breach was the 2017 Equifax incident, where attackers exploited a vulnerability in an old version of the Apache Struts web framework that Equifax had not patched; a fix for that flaw had been available for months, but because the system was outdated and unmaintained, attackers were able to use it to breach the company’s data. This illustrates how failing to update or remove obsolete components can lead to disaster.
To avoid such issues, establish a routine process (perhaps as part of quarterly maintenance or during scheduled “hardening sprints”) to prune dead code and update dependencies. Run tools that identify unused functions or detect libraries with known vulnerabilities (scanning tools and services can alert you to CVEs in your software bill of materials).
By keeping your codebase lean and up to date, you minimize the legacy risks that attackers exploit and strengthen your overall security posture.
Incident Response Plan
Even with the best preventative measures, no system is entirely immune to breaches or insider betrayal. That’s why having a well-defined incident response plan is a critical component of code security.
An incident response plan is your playbook for handling a security breach or suspected code theft. It ensures a swift, coordinated reaction that can contain and mitigate damage, preserving your business continuity and evidence for potential legal action.
Key Elements of an Effective Plan
Preparation: Define roles and responsibilities in advance. Who on your team will lead the response? Do you have contacts for external incident response specialists or legal counsel if needed? Make sure those team members are trained and aware of the procedures.
Identification: Steps to identify that an incident has occurred. This ties in with your monitoring. For example, if an alert triggers that a large amount of code was downloaded, the plan should specify how to verify if it’s a real incident and gather initial details.
Containment: Immediate actions to contain the breach. In a code theft scenario, this might mean disabling specific user accounts, revoking credentials, or temporarily blocking network access to prevent data from leaving the network. Containment also involves isolating affected systems (to prevent malware spread, etc.).
Eradication and Recovery: Once contained, work on removing the threat, e.g., ejecting an intruder from the system, eradicating malware, and fixing the vulnerabilities that were exploited. Then recover: restore systems from clean backups if needed, and resume normal operations after verifying security.
Investigation and Documentation: It’s crucial to investigate the incident and document the findings. For source code incidents, determine whose account was used, what code or data was taken or modified, and whether any backdoors were left. Document everything you find: timestamps, affected components, and likely method of exfiltration, as this evidence may be needed for legal or insurance reasons.
Notification: Depending on the severity, you may need to notify stakeholders. If customer data is compromised in a data breach, there may be legal obligations to report it (for instance, under data breach laws). In the event of trade secret theft by an employee or competitor, the appropriate course of action is to involve law enforcement (e.g., the FBI or local authorities) or file a civil lawsuit.
In 2024, for example, the U.S. Department of Justice announced charges against a former Google engineer for stealing AI-related source code to benefit companies in China. Companies in such situations often engage law enforcement through an incident response when the theft is discovered.
Follow-up: After the dust settles, hold a “lessons learned” session. What worked in the response, and what didn’t? Update the incident response plan accordingly and remediate any security gaps identified during the incident.
Practice Makes Perfect
Having this plan in writing and rehearsed (via drills or tabletop exercises) will significantly improve your organization’s resilience. The worst time to figure out what to do in a crisis is during the crisis.
By preparing in advance, you can respond decisively to security incidents, limit the impact on your business, and demonstrate to your team, customers, and, potentially, the courts that you take the protection of your source code seriously. In many jurisdictions, demonstrating robust security and an incident response plan can strengthen your case if you pursue legal action against the perpetrators of a breach.
5. Enforce Non-Compete and Non-Disclosure Agreements with Engineers and Employees
Robust employee and contractor agreements can serve as a first line of defense in preventing software and trade secret misappropriation. Two key types of agreements are Non-Disclosure Agreements (NDAs) and Non-Compete Agreements (NCAs). These, along with clauses in employment contracts around IP ownership and confidentiality, set the legal expectations that your staff must not leak or steal sensitive code or work for a competitor to exploit knowledge gained in your employ.
Make the Signing Process Meaningful
When onboarding new hires or contractors, don’t treat the signing of these agreements as a mere formality. Although many people only skim contracts, it’s wise to encourage new team members to take their time reviewing the NDA and non-compete, and to ask questions if anything is unclear.
This pause and emphasis underscore the importance of their obligations. The very act of signing, preceded by an explanation, creates a conscious understanding (and a lasting subconscious reminder) that they are bound to keep company secrets confidential and not engage in competing endeavors for a defined period. By ritualizing this process, you underscore the seriousness of protecting proprietary information.
Non-Disclosure Agreements
A well-drafted Non-Disclosure Agreement (NDA) will clearly define what information is considered confidential (e.g., source code, system architecture, algorithms, client data). It will oblige the signer not to disclose or use that information outside the scope of their work.
NDAs are ubiquitous in business, from tech companies to Hollywood. While they aren’t foolproof (someone intent on violating them can still cause harm), they provide a strong legal tool to seek damages or injunctive relief if a breach occurs. Courts tend to uphold reasonably tailored NDAs. One tip: avoid over-broad language that could render an NDA unenforceable; it should be specific enough to be fair.
Non-Compete Agreements: Proceed with Caution
Non-Compete Agreements (NCAs) are more contentious. These restrict an employee from working for competitors (or starting a competing venture) for a specified period after leaving your company, typically within a defined geographic area. NCAs can be effective at discouraging employees from taking what they’ve learned at your company to a rival.
However, in many jurisdictions, non-competes are facing increasing scrutiny and limitations. In the United States, several state legislatures have enacted laws in recent years to severely limit or ban non-compete agreements, particularly for lower-wage workers.
The FTC’s 2024 Rule
At the federal level, policy winds are changing as well. In April 2024, the Federal Trade Commission issued a final rule banning non-compete clauses for most workers (with limited exceptions, such as those tied to the sale of a business). The FTC estimated that roughly one in five American workers (about 30 million people) were bound by non-competes and argued that banning them would boost innovation and wages.
This regulatory shift means you must ensure any non-compete you use is narrowly tailored and compliant with current law. In some jurisdictions (such as California), non-competes are largely unenforceable. Always consult legal counsel to draft or update these agreements in accordance with the latest regulations.
When to Enforce Your Agreements
Even with these challenges, NDAs and NCAs (where valid) remain valuable legal tools. A narrowly drafted, reasonable non-compete that protects legitimate business interests (e.g., trade secrets or client relationships) for a short period can still be enforceable in many places. Similarly, NDAs that aren’t overly broad will generally be upheld.
It’s prudent to periodically review the agreements you have with current and former employees. If you discover a former engineer has taken a position with a direct competitor in violation of a non-compete, or you have evidence an ex-employee is using your proprietary code at their new job, do not hesitate to enforce your rights.
Often, the first step is a cease-and-desist letter reminding them of their contractual obligations. In more egregious cases, filing a lawsuit may be necessary to obtain a court injunction and damages.
High-profile tech litigation underscores the value of enforcing these agreements. When Uber hired a star engineer from Google’s Waymo unit, and he was accused of bringing Waymo’s trade secrets, Waymo sued immediately and ultimately secured a large settlement and assurances from Uber. While that case was unusually high-stakes (involving autonomous-vehicle IP), the principle applies to companies of all sizes: enforce your agreements and make clear that IP theft will not be tolerated.
In sum, strong NDAs and non-competes (combined with IP assignment clauses that make clear the company owns any work product employees create) help establish clear ownership and confidentiality of your software. They deter employees from misusing your code during or after employment. And if deterrence fails, these agreements give you a basis to pursue legal remedies against those who steal source code or divulge secrets. Be mindful to keep these agreements compliant with evolving laws, and always address confidentiality and competition within your overall onboarding/offboarding processes.
Speak With an Experienced Software Intellectual Property Attorney
You have a business to run and software to develop. Meanwhile, disgruntled employees, bad actors, and cybercriminals may exploit your focus on other tasks to erode your competitive advantage.
The best way to protect your source code and your business is to consult an intellectual property attorney experienced in software and source code protection. An experienced IP attorney can help you navigate the complex and evolving legal landscape, ensuring your employment contracts, source code policies, NDAs, and other practices comply with the law and take full advantage of available legal protections.
Why Legal Expertise Matters
This area of law changes rapidly (as noted, non-compete enforceability is shifting, and data security regulations are tightening), so it’s essential to have legal counsel review your strategies. For example, a lawyer can advise on establishing an IP portfolio (patents/trademarks) tailored to software, drafting enforceable confidentiality agreements, and implementing trade secret protection policies that hold up in court.
They can also guide you in the unfortunate event of code theft or feature copying, from coordinating with law enforcement to filing civil lawsuits under laws such as the Defend Trade Secrets Act, which provides federal remedies for trade secret theft. Having a solid legal game plan before an incident occurs means you can act quickly and decisively if something goes wrong.
Your Multi-Front Defense
The bottom line: protecting your software requires two distinct strategies that work together.
First, patent your novel functionality. This is the only protection that survives reverse engineering and cleanroom development. A competitor who understands your features can rewrite them from scratch without your code; only a patent stops them. Copyright protects your literal code, but patents protect the method itself. In the competitive SaaS landscape, where features can be studied, understood, and legally replicated, patents are your primary defensive weapon.
Second, implement the security and legal measures outlined in this article to protect your source code as a trade secret, deter employee misappropriation, and maintain your competitive advantage. Access controls, monitoring, encryption, and robust employment agreements create layers of defense against both insider threats and external attackers.
By implementing the measures discussed (identifying your unique assets, monitoring competitors, securing IP rights, locking down your codebase, and enforcing agreements), you will significantly reduce the risk of your hard-earned innovations being stolen. And by working with experienced legal professionals, you’ll be ready to respond effectively in case preventive measures aren’t enough.
In the high-stakes world of software and SaaS, where trade secret theft costs the U.S. economy up to $540 billion annually, and the Computer Software & Services industry leads all sectors in IP litigation, a proactive approach to security and IP protection is not just advisable; it’s essential for long-term success.
Your Next Steps to Software IP Protection Success
Source code theft and feature copying aren’t hypothetical threats; they’re daily realities for SaaS founders. With trade secret theft costing the U.S. economy up to $540 billion annually and the software industry leading all sectors in IP litigation, protecting your innovations is no longer optional. It’s the difference between building a defensible competitive advantage and watching competitors replicate your hard work.
The bottom line: weak IP protection helps your competitors. Strong IP protection deters them. Without proper patents, trade secret safeguards, and enforceable agreements, you’re building on shifting sand. Competitors can reverse-engineer your features, former employees can walk out with your code, and you’ll have limited legal recourse to stop them.
Here’s the critical distinction most founders miss: Even if you never lose a single line of source code, competitors can still legally replicate your features. They can study your product, understand how it works, and build their own implementation. No copyright infringement. No trade secret theft. Completely legal. The only protection against this threat is a patent on the underlying functionality. This is why patents, not just code security, must be the foundation of your IP strategy.
Every day you wait to protect your software IP is another day competitors can file patents on similar innovations, former employees can join rivals with your trade secrets fresh in mind, and bad actors can exploit security gaps in your codebase. In the first-to-file patent system, timing isn’t just important; it’s everything. The first filer prevails, regardless of who invented first.
Here’s what you need to do right now:
- Schedule a Free IP Strategy Call with our team to evaluate which software features qualify for patent protection, identify trade secret vulnerabilities in your current security practices, and develop a comprehensive protection strategy that covers both technical and legal safeguards.
- Download our SaaS Patent Guide 2.0 to understand precisely what makes software patentable, how to identify your most valuable innovations, and what timeline you’re working with for filing.
- Review your SaaS Agreement Checklist to ensure your NDAs, employment contracts, and IP assignment agreements actually protect your code and innovations.
- Audit your current security measures against the framework outlined in this article and document any gaps for immediate remediation.
- Train your staff to recognize social engineering attacks, such as an unfamiliar person bringing a suspicious flash drive into the office, to prevent unauthorized access and data theft.
Your software IP is too valuable to leave unprotected. The investments you make now in patents, trade secret protection, and security infrastructure will pay dividends when you’re raising funding (investors want to see protected IP), scaling your business (without worrying about copycats), and building long-term enterprise value.
Training your staff to recognize phishing and social engineering attacks helps protect their personal information and the organization as a whole.
At Rapacke Law Group, we work exclusively with SaaS founders and tech innovators to protect the software features and code that drive your business. Unlike traditional law firms that bill by the hour and leave you guessing about costs, we offer transparent, fixed-fee pricing for patent applications, IP strategy, and comprehensive protection plans. You’ll know exactly what you’re investing upfront; no surprise bills, no hourly meter running while you ask questions.
Get your patent filed or pay nothing. We guarantee it. We’re so confident in our ability to secure patent protection for your software innovations that if the USPTO rejects your patent application, we’ll issue a 100% refund. No questions asked.*
Don’t wait until a competitor files a patent on your innovation or a former employee shows up at a rival with your source code. Schedule your free strategy call today, and let’s build the IP protection strategy your software deserves.
To Your Success,
Andrew Rapacke, Managing Partner, Registered Patent Attorney, Rapacke Law Group
Connect with us:
LinkedIn: Andrew Rapacke – Twitter/X: @rapackelaw – Instagram: @rapackelaw
*Terms and conditions apply. Refund guarantee specific to RLG’s standard patent application services




